-
Featured services
Think beyond the robots
The successful integration of AI and IoT in manufacturing will depend on effective change management, upskilling and rethinking business models.
Read the blog -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Network Services
-
Services
Cloud
-
Services
Consulting
-
-
Services
Data and Artificial Intelligence
- AI and Intelligent Solutions
- Data/AI Strategy and Program
- Data Engineering and Platforms
- Data Governance and Management
- Data Visualization and Business Decision
- GenAI Consulting
- GenAI Platforms
- GenAI Industry Services
- GenAI Infrastructure Services
- GenAI Value Transformation
- View Data and Artificial Intelligence
-
Services
Technology Solutions
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
Services
Sustainability Services
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms

Accelerate outcomes with agentic AI
Optimize workflows and get results with NTT DATA's Smart AI AgentTM Ecosystem
Create your roadmap -
-
-
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-

Master your GenAI destiny
We’ll help you navigate the complexities and opportunities of GenAI.
Explore GenAI -
-
Master your GenAI destiny
We’ll help you navigate the complexities and opportunities of GenAI.
Explore GenAI -
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-

Everest Group PEAK Matrix® Assessment
NTT DATA is a Leader and Star Performer in the Everest Group Sustainability Enablement Technology Services PEAK Matrix® Assessment 2024.
Get the Everest report -
- Careers
The fundamental idea of a zero trust security framework is: never trust, always verify.
In the past, security followed the castle-and-moat model, where nothing outside the network could access data on the inside. When you were at the office – and therefore inside the network – you were inside the “castle”, and everything you did was trusted because of that.
Virtual private networks worked well enough to facilitate remote working when 10% or at most 20% of an organization’s workforce worked from home and the rest were at the office – safe inside the castle.
But the COVID-19 lockdowns changed all that. As more people started working from remote locations, organizations needed a new way to connect them securely to the systems and data they needed.
For example, Universal Robina Corporation (URC) Vietnam is a leader in the food and beverage industry in Vietnam with a key focus on using the cloud to adapt quickly to their changing business needs.
This includes giving their distributed workforce across the country seamless and secure access to their data and applications, wherever they are, while following a cloud-first strategy that also incorporates on-premises infrastructure.
It’s no longer enough to be connected to the network
Now, simply being connected to the network no longer matters. Instead, every time you connect to anything, the security system will check who you are, what application or data you’re connecting to, when you’re connecting, where the data resides, why the data is being accessed (the context) and how the data is being accessed.
Zero trust security constantly checks who you are and what you’re trying to access. These are the two most prominent factors it takes into account.
In a recent report titled Cyber without Perimeters, Everest Group estimates that about 65% of clients opt for an identity-based zero trust implementation. The subject’s identity is the primary component of this approach, and factors such as device location, device status, user privileges and patterns of behavior alter the policy engine’s overall confidence level.
For URC Vietnam, a zero-trust environment was ideal to give all their users secure access to their data and applications – but first they needed a partner with expertise in creating and managing a future-proof IT and security infrastructure, which can be a complex undertaking.
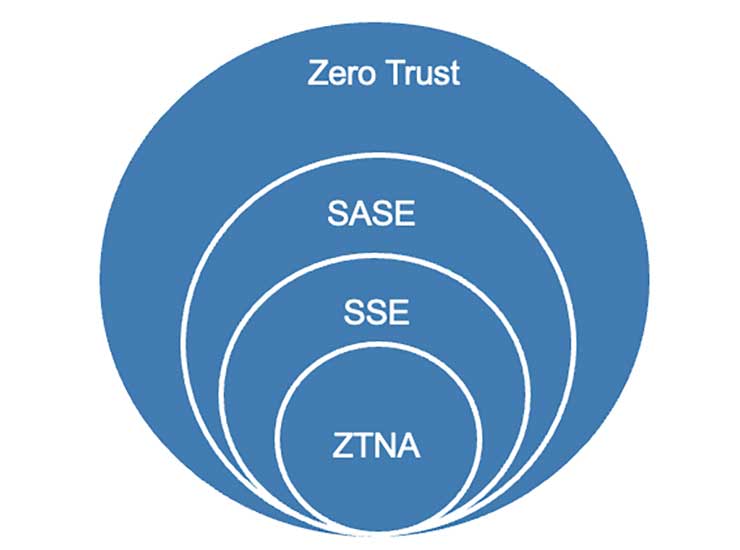
The architecture behind the acronyms
Vendors that provide zero trust security, such as Cisco, Palo Alto Networks and Zscaler, operate in an environment that is complicated by many different acronyms.
Zero trust network access (ZTNA) gives remote users secure access to internal applications.
ZTNA is part of both security service edge (SSE) - cloud-delivered security services for the network – and secure access service edge (SASE). By converging networking and security services into a single, cloud-delivered service model, SASE adds an element of secure access with software-defined wide-area networks (SD-WAN) provided by Cisco, for example.
The overall zero trust layer is made up of policies and procedures – such as making sure not only that users have access to applications but that those applications are allowed to interact too. An attacker who gets into your network might get one application to speak to another if you have not implemented full zero trust.
Shifting the security barrier to the cloud
Many organizations’ legacy technology solutions allowed them to follow the VPN-based castle-and-moat approach. Users with a token on their phones would log in and access the entire network.
To make zero trust security work, organizations had to segment their network environments and break down the singular-trust approach into smaller zones of implicit trust. This meant employees in HR could use only HR applications, and similar limitations applied to people in other departments.
A fundamental issue with zero trust in the beginning was the suggestion to segment the network by putting more and more firewalls inside a data center. However, the network itself often ran at far higher speeds than the internal firewalls, which caused delays – so no one bought the firewalls.
Now, we've moved large volumes of data from internal data centers to the cloud, where we have virtual firewalls connected to virtual networks with virtual data centers in a virtual computing space. In this environment, you’re limited only by the budget required to gain the speed and computing power you need.
Effectively, we’ve shifted the security barrier to a different area – but you still need to have technical controls in place.
Your management console must be the same version or higher than the firewalls you’re trying to manage. There’s always a need for patches and updates. But if the management console is supported and run from the cloud, then you don’t need to keep updating it. You always have the latest version, so there’s much less need for change management.
Your old firewall just won’t do
Because we all want access to the internet, security teams have to follow the zero trust approach to make sure we don’t connect to anything malicious.
We also want to make sure that our business applications are secure. So, when it comes to sharing information between colleagues and with authorized third parties, like customers, we need a control layer to direct them only to what they are allowed to access.
In this environment, some security controls have now moved closer to the websites or applications they protect, or to the cloud itself.
This shift in location means that your traditional firewall is likely to be in the wrong place and too slow to keep up with the load.
Even so, you might believe your firewall is still serviceable. But imagine you have an old phone and can’t update the operating software anymore. When your Facebook app stops working as it’s no longer supported, suddenly your phone becomes far less useful.
In the world of security, if a firewall can’t be updated anymore, it can’t protect you against every new threat coming your way. Also, in highly regulated environments such as financial services, you may not even be allowed to have unsupported devices in your network because of corporate governance.
Sustainability is another consideration: a server you bought six years ago might be the same size as the one you’ll buy now, but the new one uses less power and is probably several times faster, so you need fewer servers altogether to achieve the same outcome.
Assessments without backup expertise are pointless
There are many complexities at play here. You may have bought your technology from multiple vendors, using different budgets linked to teams in your business that still work in silos. For example, the cloud team won’t necessarily inform the security team about changes in the cloud, and the security team’s efforts may then not extend to the virtual cloud network.
This is why organizations choose to work with an experienced third party to complete a cloud and cybersecurity assessment. Our approach at NTT is to identify key areas in your organization to establish how secure you are now, where the pain points are and what level of security you need – and, of course, how that aligns with your technology and cloud strategy.
The time needed for such an assessment depends on the size of your organization. There’s no reason to rush through it, because cybersecurity is vital to the long-term success of your business.
Another benefit of working with a provider like NTT is that, apart from our cybersecurity insights, we also bring a range of cloud and network expertise to the table, so you benefit from a much more holistic approach.
Added to that are our close relationships with technology vendors. Our technology partnership with Cisco has lasted for more than 30 years, spanning full-stack solutions and services from infrastructure to applications and serving 75% of Fortune 100 companies.
This allows us to co-innovate where networks, cloud and applications converge – including in robust cybersecurity – and offer our clients the benefit of our reach and experience. We’ll enable your hybrid workforce to work productively and securely from anywhere.
Read more about NTT’s Network Consulting Services to see how you can transform your network to underpin your cloud-to-edge infrastructure.