-
Featured services
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Network Services
-
Services
Cloud
-
Services
Consulting
-
-
Services
Data and Artificial Intelligence
- AI and Intelligent Solutions
- Data/AI Strategy and Program
- Data Engineering and Platforms
- Data Governance and Management
- Data Visualization and Business Decision
- GenAI Consulting
- GenAI Platforms
- GenAI Industry Services
- GenAI Infrastructure Services
- GenAI Value Transformation
- View Data and Artificial Intelligence
-
Services
Infrastructure Solutions
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
Services
Sustainability Services
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms
![]()
Accelerate outcomes with agentic AI
Optimize workflows and get results with NTT DATA's Smart AI AgentTM Ecosystem
Create your roadmap -
-
-
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
-
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
- Careers
Topics in this article
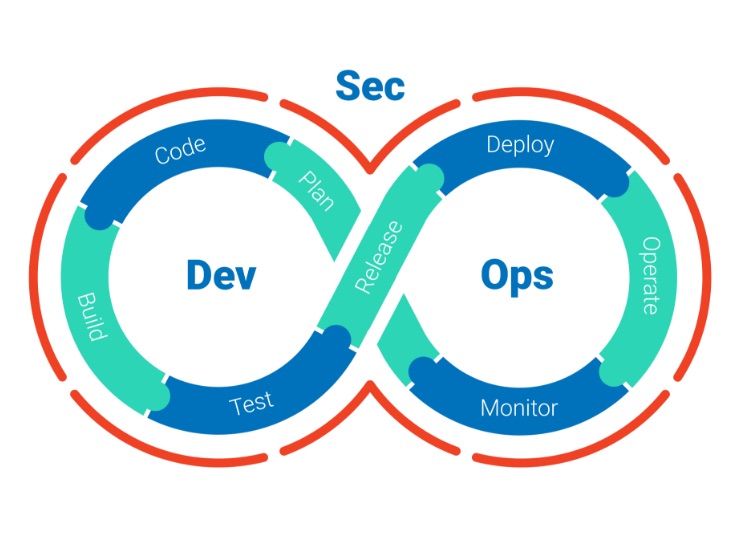
How application security can validate your digital journey
A recent NTT Threat Report1 spoke about the ‘digital wild west’ and how digital transformation has meant that organizations, irrespective of their core business function, are ‘all software companies now’. COVID-19 has exacerbated this, being an unexpected driver of further digital adoption as organizations were forced to react to a very different 2020.Align this with findings from our annual Global Threat Intelligence Report – which identified that 55% of all global attacks are now at the application layer – it’s clear that many organizations are facing the challenge of maximizing business opportunities while balancing new forms of business risk.
Security testing is a more effective weapon at combatting web application vulnerabilities and reducing an organization’s attack surface, than traditional, reactive and compensating controls. However, as outlined in the report, the variety of security testing techniques come with their own challenges.
So, how can organizations overcome these challenges and make the shift towards security being a key tenet of overall business strategy, where security gaps are proactively identified, and security controls are up to date?
My recommendation is a robust and comprehensive software assurance program: one which not only includes application security testing, but also has an equal focus on people and process. This means the program can provide broad coverage of software development, from design to operation.
Steps to building a comprehensive software assurance program
As a critical first step, a software assurance program that considers people, process and technology requires organizational buy in from senior stakeholders. Organizational security must be considered as a shared responsibility, just like quality, performance and functionality. Being seen as an equal bedfellow will provide the security team the impetus it needs to positively impact the software development lifecycle.
Software assurance then needs to be measured. Unless an organization has visibility of their strengths and weaknesses, what controls are currently in place and where the gaps are, an actionable plan can’t be created. To help organizations achieve this, there are maturity models such as Building Security in Maturity Model (BSIMM) and Open Web Application Security Project (OWASP) Security Assurance Maturity Model (SAMM), which are yardsticks to benchmark organizations against known security assurance practices.
Both models help identify current and target maturity levels, across security disciplines. A clear and measurable plan can then be put in place to improve the software security posture of an organization. Take OWASP SAMM as an example. This framework has been designed to be flexible and easy to follow. While it’s a prescriptive model, OWASP encourages organizations to define their own required maturity state and doesn’t insist maximum maturity is achieved across the board. It’s broken down into business functions and security practices, to ensure organizations can take an iterative approach to security.
What might a mature software assurance program look like?
Some initial recommendations I would offer to get things started are:
- Consider all the phases of the software development life cycle (SDLC), not just the test phase. For example, threat modelling in the design phase will ensure risks are understood early in the application lifecycle and mitigations or controls identified upfront. Look to map security activities across the whole application lifecycle. External resources, such as those offered by OWASP or SANS, can help map these activities to the right DevOps phases.
- Consider the actors involved. Developers aren’t security experts and, equally, security experts aren’t developers. A well-defined, role-based training program will help foster the culture required to succeed. For example, secure coding training for developers and SDLC tooling training for security engineers.
- Nominate a security champion. Where organizations are benefitting from DevOps methodologies, a security champion can forge a bond between the security and development teams. As security professionals are often outnumbered in organizations by their IT/DevOps colleagues,2 the security champion can be an extension of the security function into a development squad, and can provide more timely and consistent security assurance during the delivery lifecycle.
- Build a secure process framework. This will empower developers and security professionals alike to make best use of the technology provided to them. A repeatable set of processes, (preferably automated) ensures a consistent and repeatable approach with suitable guardrails agreed in advance.
Application security testing is critical to validating an organization’s attack surface and securing their digital journey. But an organization-wide, holistic approach, where people, process and technology are brought together to ensure security is considered to be a process, not a goal, helps organizations become secure by design.
As one of the all-time great French footballers, Michel Platini, once said, ‘A football team represents a way of being, a culture’ – and so too does a mature software assurance program.
1Monthly Threat Report November 2020
2Companies are making up for lack of cybersecurity professionals by investing in their developers