-
Featured services
Think beyond the robots
The successful integration of AI and IoT in manufacturing will depend on effective change management, upskilling and rethinking business models.
Read the blog -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Network Services
Popular Products
-
Services
Cloud
Popular Products
-
Cloud Architecture and Modernization
Discover how to achieve your business goals through cloud modernization practices, that deliver improved agility, reusability and scalability.
-
Cloud Optimization
Discover how to maximize operational excellence, business continuity and financial sustainability through our cloud-advanced optimization services.
-
-
Services
Consulting
-
-
Services
Data and Artificial intelligence
- AI and Intelligent Solutions
- Data/AI Strategy and Program
- Data Engineering and Platforms
- Data Governance and Management
- Data Visualization and Business Decision
- GenAI Consulting
- GenAI Platforms
- GenAI Industry Services
- GenAI Infrastructure Services
- GenAI Value Transformation
- View Data and Artificial Intelligence
-
Services
Technology Solutions
Client stories
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
Services
Sustainability Services
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms

Master your GenAI destiny
We’ll help you navigate the complexities and opportunities of GenAI.
Explore GenAI -
-
-
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-

Master your GenAI destiny
We’ll help you navigate the complexities and opportunities of GenAI.
Explore GenAI -
-
Master your GenAI destiny
We’ll help you navigate the complexities and opportunities of GenAI.
Explore GenAI -
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-

Everest Group PEAK Matrix® Assessment
NTT DATA is a Leader and Star Performer in the Everest Group Sustainability Enablement Technology Services PEAK Matrix® Assessment 2024.
Get the Everest report -
- Careers
- Developers aren’t writing secure code because they aren’t taught to do so, nor do they think about how hackers can access and use the code/data they create.
- Developers aren’t trained to adapt best of agile and security practices to address vulnerabilities before they become a problem.
- Most organizations are struggling to balance agility and security and are not implementing security by design.
- Security and development teams don’t have access to the right automated tools and platforms that help to establish an effective cybersecurity program.
- There’s a lack of awareness and visibility into how the third-party apps are using, sharing or selling the data you collect.
- Business leaders or app owners aren’t providing enough transparency on how they protect personal data nor are they providing guidelines on how to have more control over data usage.
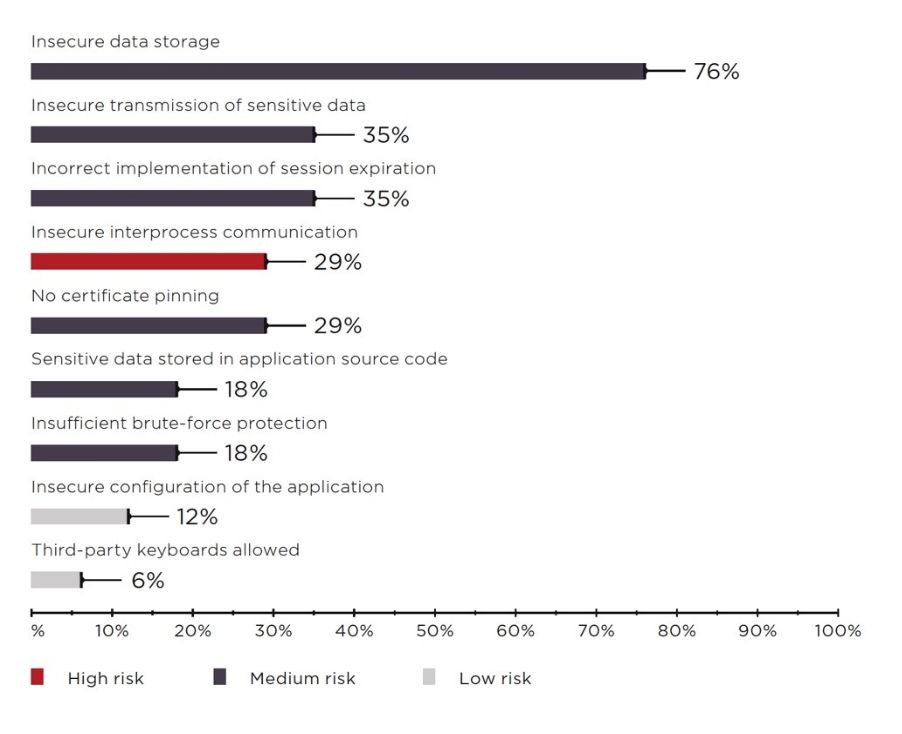
Mobile application vulnerabilities (percentage of client-side components)
Source: ptsecurity.com
Why PII Security Matters
Data breaches are becoming everyday news and the ramifications of data breaches can be far-reaching and can last for years. A substantial number of hacking attacks are through exploited application security vulnerabilities; cybercriminals often go after users’ personally identifiable information (PII), user credentials, and financial and medical information to perform multiple types of frauds and identity theft.
Eduardo Cervantes, Manager Sentinel Mobile at NTT Application Security says, ‘The impact of data abuse can be on individual level, business level or societal level. An individual could be a subject of identity theft, fraud or a serious crime if a malicious threat actor lays hands on personal data that’s collected by your app. On a business level it could be competitive situation where one app leverages user data to gain an unfair advantage. Social impact can be immense and far reaching. Take for example the Cambridge Analytica data scandal where the political firm accessed private data of millions of Facebook users to influence elections. It’s important to protect user data and be aware that your app could be contributing to a much larger problem if the stored data can be hacked, stolen or leaked.’
Collecting large datasets creates increased risks and most security teams and app developers are not aware of best practices on protecting PII and the implications of sensitive data sharing.
We’d would like to offer you a couple of best practices that security engineers and development teams can follow to strengthen your application security and overall security posture (learn more in our webinar) :
-
Best practise 1: Implement security by design
Most apps collect data that far exceeds what’s necessary for the app. How does this indiscriminate collection of sensitive data increase the risk for your customers and business?
Use these best practices to reduce the risk to user data:
- Collect data only what is required.
- Collect in a responsible way. Know the difference between sensitive and non-sensitive data.
- Secure the collection and storage of the data.
- Evaluate how long you should retain this data.
- Practice rigorous vetting of third-party providers to check on how they use the data that you collect.
- And above all, educate developers on secure coding practices.
Security best practices must be developed even before planning, design and coding. How can you make your code less vulnerable? Test for vulnerabilities throughout the software development lifecycle. Implementing security by design and providing the right tools to your developers to vet the apps earlier in the software lifecycle helps prevent security gaps as the applications are designed, developed and tested.
As a security engineer, mobile app developer or mobile app business owner, you must take all steps to implement guidelines and best practices on collection, sharing and storage of sensitive data. The more the developers integrate security into the design, the safer applications can be pushed to production.
Learn more about the top 10 vulnerabilities in mobile applications.
- Best practice 2 – Security first; compliance will follow
Organizations that can’t handle the security of the sensitive data are bound to lose trust and that’s a huge risk to their business survival. Data compliance regulations and the penalties of non-compliance are making companies think more carefully about what sensitive data they collect, share and how they secure it.
With GDPR, CCPA, and other data protections laws are here to ensure industry-wide privacy regulations, companies need to be more aware of what data they keep and how it’s stored. App owners need to understand the data that they have on all of their users. And they must communicate to the user how the data will be used, including third-party usage.
Checkbox compliance doesn’t mean that you’re holistically secure, but it’s a beginning to ensure that you’re doing due diligence to protect sensitive data.
The National Institute of Standards and Technology (NIST) offers specific security-focused guidance on how organizations can minimize their mobile app risks. Over the last few years, NIST has been updating their app-vetting recommendations to emphasize the need to have security and privacy built-in by design. The NIST Privacy Framework provides recommendations and best practices on how organizations can ensure the security of mobile applications and address security weaknesses.
As a business owner, app developer or member of a security team, we can do better. Let’s practice what we preach to protect sensitive data, meet compliance and continue to invest in platforms and services that help secure applications, networks and devices. It’s time to take mobile security and data privacy seriously.
We continued this discussion in our webinar. Join us on a PII journey to gain a deeper understanding on why data privacy matters and why you should care about protecting user data. We’ll also share some best practices on data collection and mobile AppSec.
View the webinar.